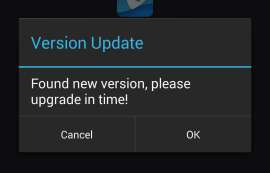
Figure 1: New Wave Version Dialog
Dr. Georg Lukas, rt-solutions.de GmbH, 2016-03-16
Affected app: Grandstream Wave version 1.0.1.26 (and probably earlier)
Classification:
The Grandstream Wave app periodically queries the Grandstream server for app updates. If a new update is found, the app shows a notification to the user that either opens the app's Google Play page or auto-downloads the APK file and opens it for installation.
The update information is downloaded over an insecure connection from media.ipvideotalk.com and contains the version code and the update URL. An active attacker can redirect this request and trick the user into downloading a malicious update package. Users that have "Unknown Sources" enabled in the Android security preferences, or enable it upon request, can be tricked into installing a malicious application that disguises itself as a Wave update.
The Grandstream Wave app downloads an update info XML on each app start. The address is hardcoded in the application properties as follows:
updateinfo_serverurl=http://media.ipvideotalk.com/upgrade/updateinfo.xmlThis file was last updated in March 2015 and contains the following outdated information:
<?xml version="1.0" encoding="utf-8"?>
<info>
<version>1.0.1.6</version>
<versioncode>69</versioncode>
<updateurl>market://details?id=com.softphone</updateurl>
<description>检测到最新版本,请及时更新!</description>
</info>The version available via Google Play at time of this writing is 1.0.1.26 (versioncode 89), therefore no update dialog will be shown by the application.
Internally, the XML is processed by the app as follows:
versioncode is higher than the app's.
Figure 1: New Wave Version Dialog
updateurl contains "market://details", open the Google Play page for the app's package (this is secure, the URL from the XML is not used).updateurl to /sdcard/GSWave/upgrade/GSWave.apk (figure 2) and open an installation dialog.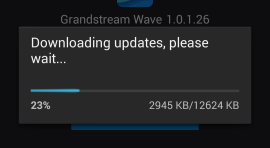
Figure 2: Download of New Version
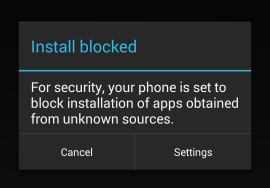
Figure 3: Android Security Settings
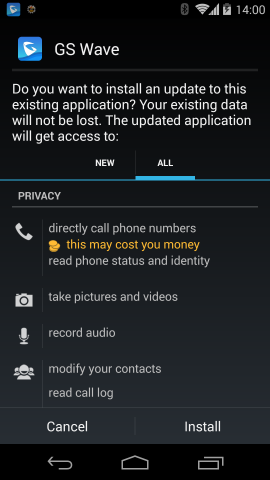
Figure 4: Upgrade of Official Wave App
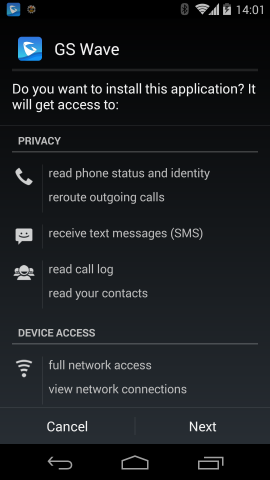
Figure 5: Installation of Malicious App
As from the user's perspective this is an update to a trustworthy app, which was initiated by the app itself, there is no reason to mistrust the installation and to question the permissions asked by the installer.
With a one-time Man-in-the-Middle attack, it is possible to trick the user into installing a malicious Android application with permissions to make phone calls, access the contact data, recording audio and video and much more. Such an application can perform extensive surveillance of the user afterwards.
It is not possible to disable update checks in the Wave application. Therefore, no technical mitigation mechanisms are possible. However, the following steps can be undertaken to reduce risk:
Please contact with any further questions regarding this vulnerability.