Georg Lukas, 2024-05-22 18:04
Starting in 2009, Samsung has created a wide range of compact cameras with built-in WiFi support, spread over multiple product lines. This is a reference and data collection of those cameras, with the goal to understand their WiFi functionality, and to implement image uploads on the go.
This is a follow-up to the Samsung NX mirrorless archaeology article, which also covers the Android-based compact cameras.
If you are in Europe and can donate one of the "untested" models, please let me know!
Model Line Overview
Samsung created a mind-boggling number of different compact cameras over the years, apparently with different teams working on different form factors and specification targets. They were grouped into product lines, of which only a few were officially explained:
- DV: DualView (with a second LCD on the front side for selfies)
- ES: unknown, no WiFi
- EX: high-end compact (maybe "expert"?)
- NV: New Vision, no WiFi
- MV: MultiView
- PL: unknown, no WiFi
- SH: unknown
- ST: Style feature
- WB: long-zoom models

Quite a few of those model ranges also featured cameras with a WiFi controller, allowing to upload pictures to social media or send them via email. For the WiFi-enabled cameras, Samsung has been using two different SoC brands, with multiple generations each:
Zoran COACH ("Camera On A CHip") based on a MIPS CPU.
DRIM engine ("Digital Real Image & Movie Engine") ARM CPU, based on the Milbeaut (later Fujitsu) SoC.
WiFi Cameras
This table should contain all Samsung compacts with WiFi (I did quite a comprehensive search of everything they released since 2009). It is ordered by SoC type and release date:
| Camera | Release | SoC | Firmware | Upload Working |
|---|---|---|---|---|
| Zoran COACH (MIPS) | ||||
| ST1000 | 2009-09 | COACH 10 | N/A | ❌ unknown serviceproviders API endpoint |
| SH100 | 2011-01 | COACH ?? | 1107201 | ✔️ (fw. 1103021) |
| ST200F | 2012-01 | COACH 12: ZR364249NCCG | 1303204 | ✔️ Yahoo (fw. 1303204(*)) |
| DV300F | 2012-01 | COACH 12 | 1211084 | ✔️ (fw. 1211084) |
| WB150F | 2012-01 | COACH 12 ML? | 1208074 | ✔️ (fw. 1210238) |
| WB35F, WB36F, WB37F | 2014-01 | COACH 12: ZR364249BGCG | N/A | ✔️ MSN (WB35F 1.81; WB37F 1.60 and 1.72) |
| WB50F | 2014-01 | COACH ?? | N/A | ✔️ MSN cookie (fw. 1.61) |
| WB1100F | 2014-01 | COACH 12: ZR364249BGCG | N/A | ✔️ MSN (fw. 1.72?) |
| WB2200F | 2014-01 | COACH ??: ZR364302BGCG | N/A | 🤷 email (fw. 0.c4) |
| Milbeaut / DRIM engine (ARM) | ||||
| WB850F | 2012-01 | DRIM engine III? | 210086 | ✔️ Yahoo (fw. 210086) |
| EX2F | 2012-07 | DRIM engine III | 1301144 | ✔️ Yahoo (fw. 303194) |
| WB200F | 2013-01 | Milbeaut MB91696 | N/A | ✔️ hotspot (fw. 1411171) ✔️ MSN (fw. 1311191) |
| WB250F | 2013-01 | Milbeaut MB91696 | 1302211 | ✔️ (fw. 1302181) |
| WB800F | 2013-01 | Milbeaut MB91696 | 1311061 | ✔️ MSN redirect (fw. 1308052) |
| DV150F | 2013-01 | Milbeaut MB91696 | N/A | ✔️ MSN redirect (fw. 1310101) |
| ST150F | 2013-01 | Milbeaut MB91696 | N/A | ✔️ MSN redirect (fw. 1310151) |
| WB30F, WB31F, WB32F | 2013-01 | Milbeaut M6M2 (MB91696?) | 1310151 | ✔️ hotspot (WB31F fw. 1310151(**)) |
| WB350F, WB351F | 2014-01 | Milbeaut MB865254? | N/A | ✔️ (WB351F fw. GLUANC1) |
| WB380F | 2015-06? | Milbeaut MB865254? | N/A | ✔️ (fw. GLUANL6) |
| Unknown / unconfirmed SoC | ||||
| MV900F | 2012-07 | Zoran??? | N/A | untested |
| DV180F | 2015? | same Milbeaut as DV150F? | N/A | untested |
Legend:
- ✔️ = works with samsung-nx-emailservice.
- ✔️ Yahoo/MSN = works with a respective cookie response.
- ❌ hotspot = camera mis-detects a hotspot with a login requirement, opens browser.
- 🤷 WB220F = there is a strange issue with the number of email attachments
- untested = I wasn't (yet) able to obtain this model. Donations are highly welcome.
- pending = I'm hopefully going to receive this model soon.
- (*) the ST200F failed with the 1203294 firmware but worked after the upgrade
- (**) the WB31F failed with the 1411221 firmware but worked after the downgrade to the WB30F firmware 1310151! to 1303204.
- "N/A" for firmware means, there are no known downloads / mirrors since Samsung disabled iLauncher.
- "fw. ???" means that the firmware version could not be found out due to lack of a service manual.
There are also quite a few similarly named cameras that do not have WiFi:
- DV300/DV305 (without the F)
- ST200 (no F)
- WB100, WB150, WB210, WB500, WB600, WB650, WB700, WB750, WB1000 and WB2100 (again, no F)
Hotspot Detection Mode
Most of the cameras only do a HTTP GET request for http://gld.samsungosp.com
(shut down in 2021) before failing into a browser. This is supposed to help
you login in a WiFi hotspot so that you can proceed to the upload.
Redirecting the DNS for gld.samsungosp.com to my own server and feeding back
a HTTP 200 with the body "200 OK", as
documented in 2013 doesn't help to
make it pass the detection.
There is nothing obvious in the PCAP that would indicate what is going wrong there, and blindly providing different HTTP responses only goes this far.
Update (May 2025): Samsung changed the server response to return an empty payload in October 2014 (between NX mini firmware 1.07 and 1.08), and added a firmware check for ETag header, Server=nginx, length=0.
Brief Firmware Analysis
Samsung used to provide firmware through the iLauncher PC application, which downloaded them from samsungmobile.com. The download service was discontinued in 2021 as well. Most camera models never had alternative firmware download locations, so suddenly it's impossible to get firmware files for them. Thanks, Samsung.
The alternative download locations that I could find are documented in the firmware table above.
Obviously, the ZORAN and the DRIMe models have different firmware structure.
The ZORAN firmware files are called <model>-DSP-<version>-full.elf but
are not actually ELF files. Luckily,
@jam1garner already analyzed the WB35F firmware
and created tools to dissect the ELFs.
Unfortunately, none of the inner ELFs seem to contain any strings matching the
social media upload APIs known from
reverse-engineering the upload API.
Also the MIPS disassembler seems to be misbehaving for some reason, detecting
all addresses as 0x0:
int DevHTTPResponseData(int param_1,int param_2,int param_3)
{
/* snip variables */
if (uRam00000000 != 0) {
(*(code *)0x0)(0,param_1);
}
(*(code *)0x0)(0,param_1,param_3);
if (uRam00000000 != 1) {
(*(code *)0x0)(param_2,param_3);
...
The DRIMe firmware files follow different conventions. WB850F and EX2F images are uncompressed multi-partition files that are analyzed in the WB850F reverse engineering blog post.
All other DRIMe models have compressed DATA<model>.bin files
like the NX mini, where an
anlysis of the bootloader / compression mechanism needs to be performed prior
to analyzing the actual network stack.
Update (June 2025): the NX mini and NX3000/NX3300 models use the
M7MU firmware format, and all models wih the
DATA<model>.bin file format have the actual code compressed using
Fujitsu RELC.
Yahoo! Hotspot Detection
Some models (at least the ST200F and the WB850F) will try to connect to
http://www.yahoo.co.kr/ instead of the Samsung server. The WB1100F will
load http://www.msn.com/. Today, these sites will redirect to HTTPS,
but the 2012 cameras won't manage modern TLS Root CAs and encryption, so they
will fail instead:
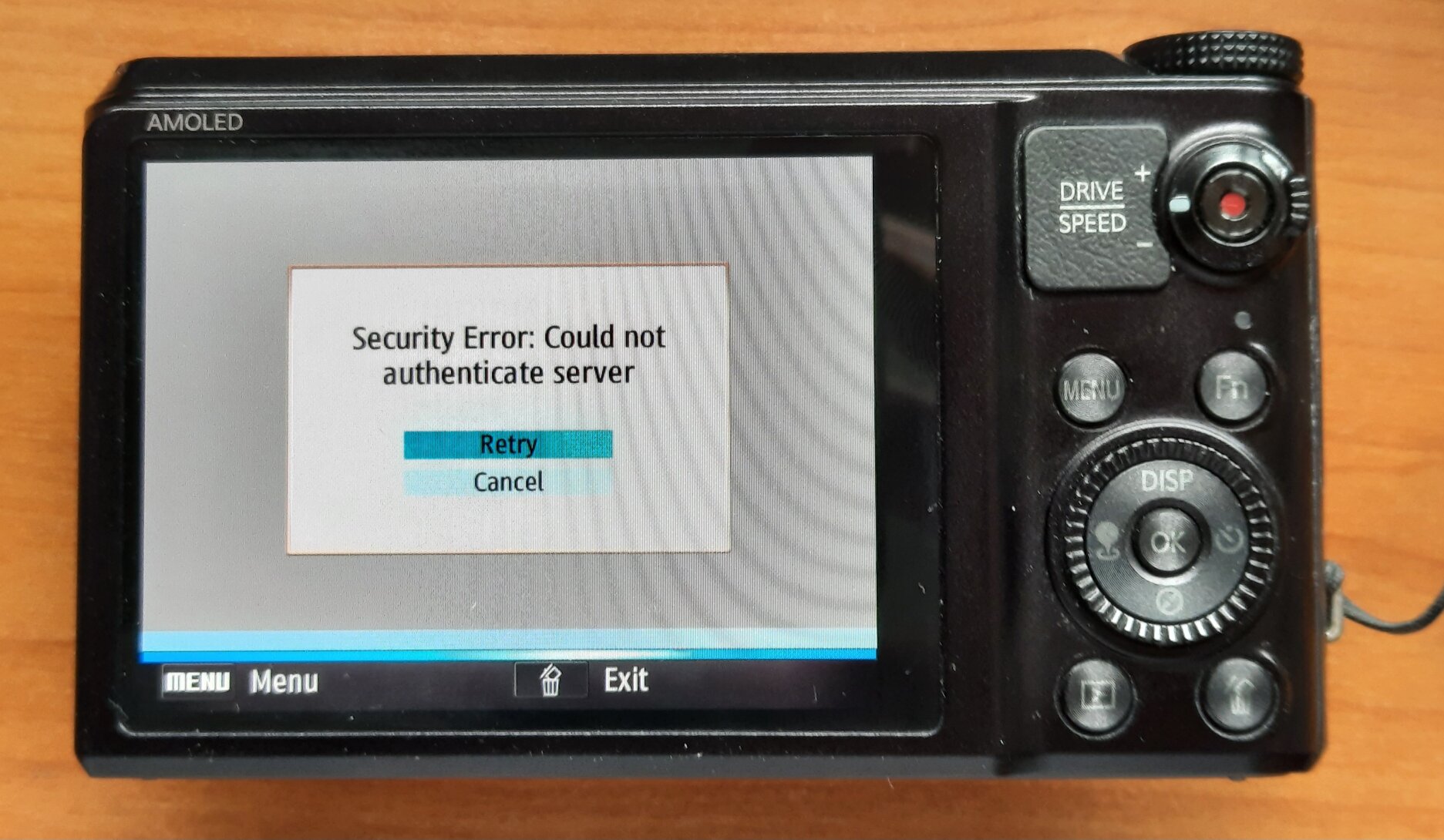
Redirecting the Yahoo hostname via DNS will also make them connect to our magic
server, but it won't be detected as proper Yahoo!, showing the hotspot
detector. Preliminary reverse engineering of the uncompressed WB850F firmware
shows that the code checks for the presence of the string domain=.yahoo in
the response (headers). This is normally a part of a cookie set by the server,
which we can
emulate to pass the hotspot check.
Similarly, it's possible to send back a cookie for domain=.msn.com to pass
the WB1100F check.
Screw the CORK
The Zoran models have a very fragile TCP stack. It's so fragile that it won't
process an HTTP response served in two separate TCP segments (TCP is a byte
stream, fragmentation into segments should be fully abstracted from the
application). To find that out, the author had to compare the 2014 PCAP with
the PCAPs from samsung-nx-emailservice line by line, and see that the
latter will send the headers and the body in two TCP segments.
Luckily, TCP stacks offer an "optimization" where small payloads will be
delayed by the sender's operating system, hoping that the application will add
more data. On Linux, this is called TCP_CORK
and can be activated on any connection.
Testing it out of pure despair
suddenly made at least the ST200F and the WB1100F work. Other cameras were
only tested with this patch applied.
GPS Cameras
Of the WiFi enabled models, two cameras are also equipped with built-in GPS.
The ST1000 (also called CL65 in the USA), Samsung's first WiFi model, comes with GPS. It also contains a location database with the names of relevant towns / cities in its firmware, so it will show your current location on screen. Looks like places with more than ~10'000 inhabitants are listed. Obviously, the data is from 2009 as well.
The WB850F, a 2012 super-zoom, goes even further. You can download map files from Samsung for different parts of the world and install the maps on the SD card. It will show the location of taken photos as well, but not from the ones shot with the ST1000.

And it has a map renderer, and might even navigate you to POIs!
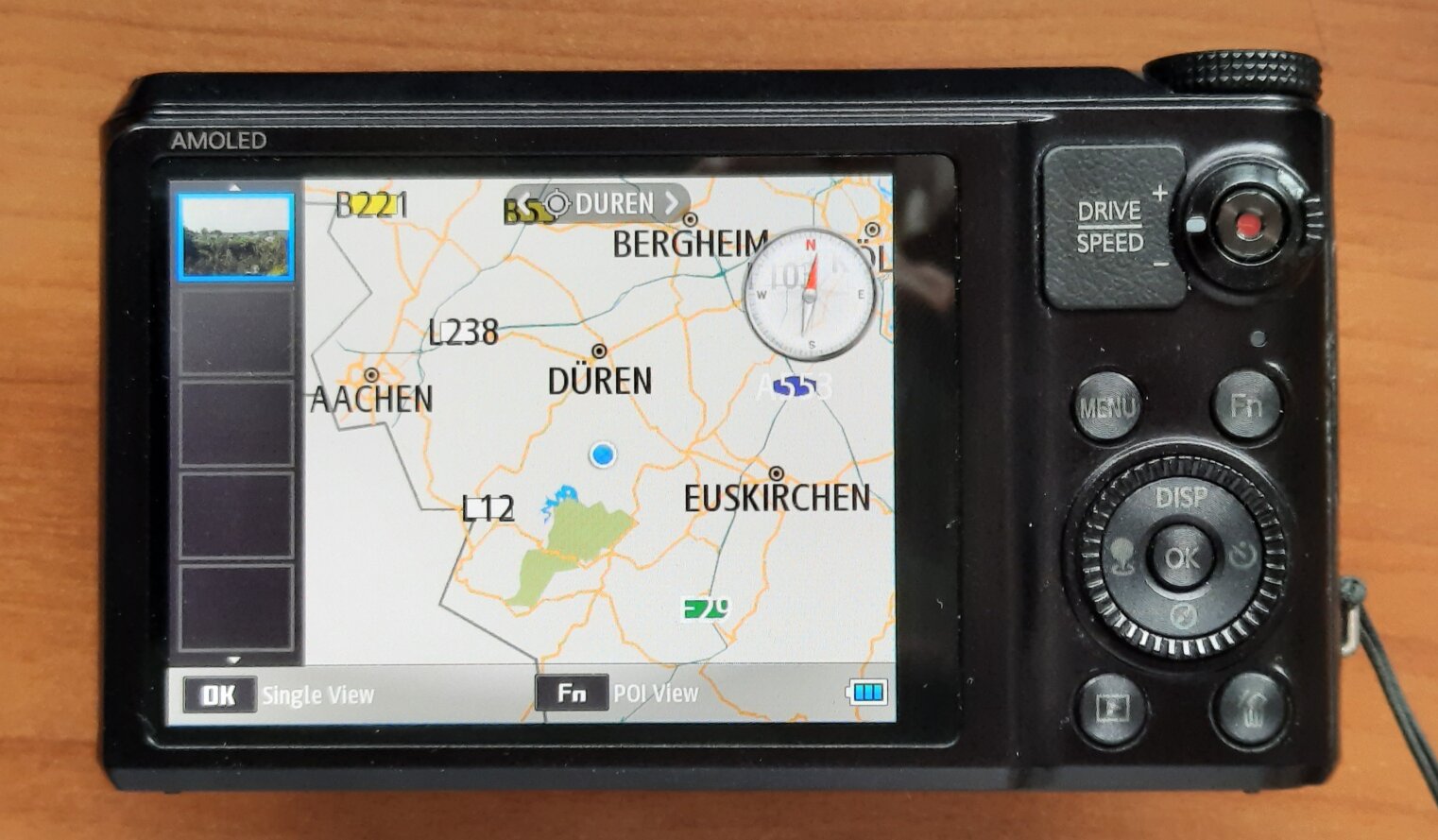
WiFi Camcorders
Yes, those are a thing as well. It's exceptionally hard to find any info on them. Samsung also created a large number of camcorders, but it looks like only three models came with WiFi.
From a glance at the available firmware files, they also have Linux SoCs inside, but they are not built around the known ZORAN or DRIMe chips.
The HMX-S10/S15/S16 firmware contains a number of S5PC110 string references, indicating that it's the Exynos 3110 1GHz smartphone CPU that also powered a number of Android phones.
The QF20 and QF30 again are based on the well-researched Ambarella A5s. The internet is full of reverse-engineering info on action cameras and drones based on Ambarella SoCs of all generations, including tools to disassemble and reassemble firmware images.
The QF30 is using a similar (but different!) API as the still cameras, but
over SSL and without encrypting the sensitive XML elements, and does not accept
the <Response> element yet.
| Camera | Release | SoC | Firmware | Working |
|---|---|---|---|---|
| HMX-S10, HMX-S15, HMX-S16 | 2010-01 | Samsung S5PC110/Exynos 3110(??) | 2011-11-14 | untested |
| HMX-QF20 | 2012-01 | Ambarella A5s | 1203160 | untested |
| HMX-QF30 | 2013-01 | Ambarella A5s | 14070801 | ✔️ SSLv2 (fw. 201212200) |
Legend:
- ✔️ SSLv2 = sends request via SSLv2 to port 443, needs something like socat23
